Products
Buy options
€18.00| Model Number | T2F2-mini |
|---|---|
| Certification |  |
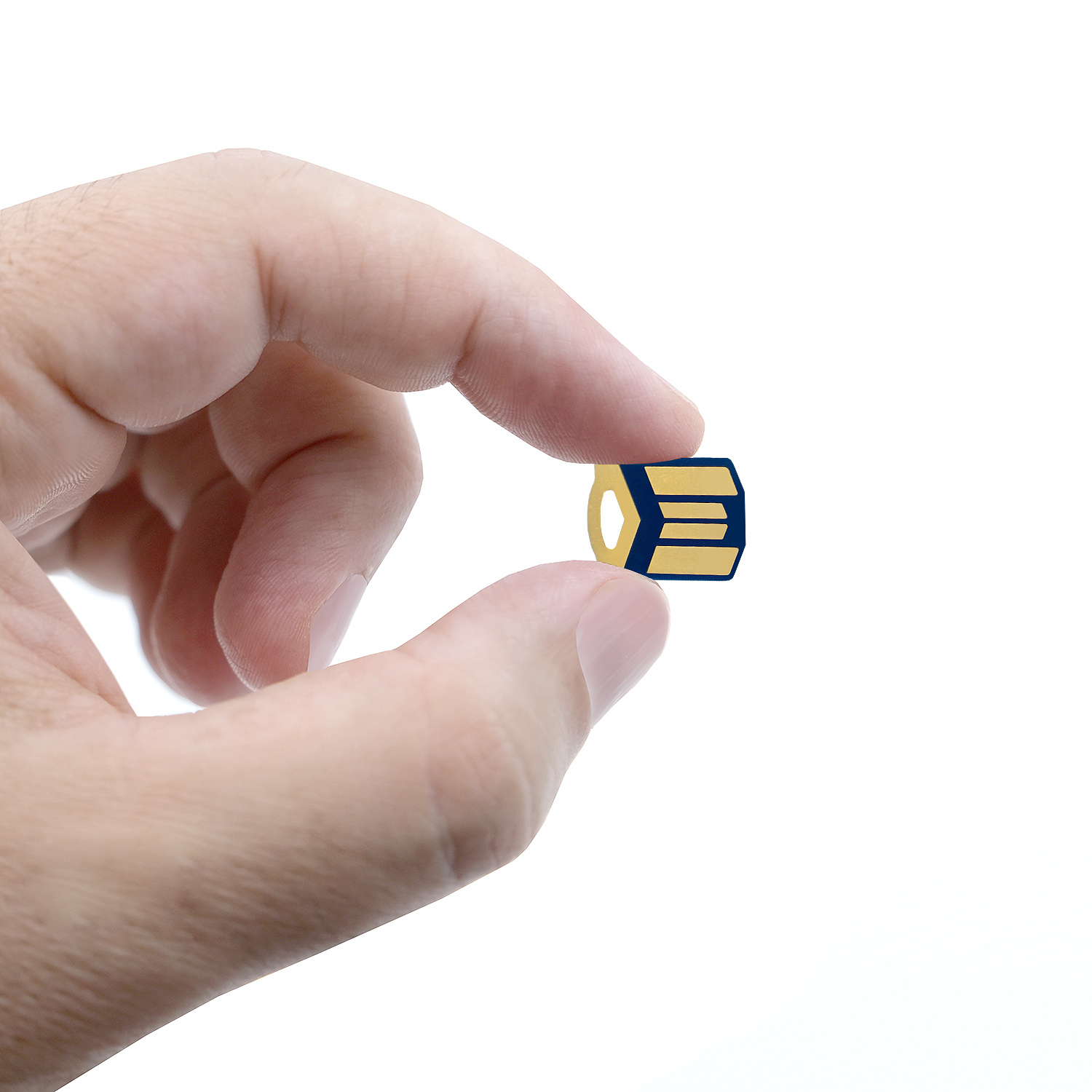
| Form-factor | mini form factor fitting into USB-A port |
| Functions | FIDO2.1PRE WebAuthN+CTAP |
| Dimensions | 15x12x4 mm |
| Weight | 8 gr |
| Programmable | |
| Storage |
passkeys: 128 HOTP: 1 TOTP: 0 |
| Product ID | T2-69 |
| Azure Passwordless | fully compatible | |
|---|---|---|
| Google Account | fully compatible | |
| Stripe Account | fully compatible | |
| Facebook Account | fully compatible | |
| GitHub Account | fully compatible | |
| 🇨🇭 AGOV- Authentication of Swiss Authorities | fully compatible | |
This list is far from complete; we only highlight some featured supported systems. Listing all compatible systems would make the list very long. Check with us for more details: |
contact us |
|
If the system you are using is not included in the compatibility list, it does not necessarily indicate incompatibility. We encourage you to refer to our integration guides page or get in touch with us for more information. | ||
For detailed information on how FIDO2 authentication is supported across different operating systems and browsers, including specific considerations and limitations, please visit our comprehensive guide
Please check product and platform compatibility before placing an order
All pictures shown are for illustration purpose only. Actual product may slightly vary due to product enhancement or other reasons.
FIDO security keys are small USB dongles that enable secure login to websites and applications supporting FIDO2 WebAuthn and classic FIDO (U2F) standards. Token2 T2F2-mini is our smallest FIDO2 key (only 15x12x4mm) and is running FIDO2.1pre firmware. Token2 T2F2-mini security key combines hardware-based authentication, public-key cryptography, HOTP, U2F, and FIDO2 protocols to protect your accounts. This type of security devices provides the highest level of multi-factor authentication of user accounts with Twitter, Facebook, Gmail, GitHub, Dropbox, Dashlane, Salesforce, Duo, Centrify and hundreds more HOTP, U2F, and FIDO2 compatible services. No additional tools or applications are required and the login process is simple and reliable. Just insert the Security Key into a USB-A slot and authenticate with a simple touch. We also sell a compact USB-A to Type-C adapter, so you can use the same key with devices with USB-Type-C slots. The T2F2 security key does not require a battery nor network connectivity, so it is always on and accessible.
Specifications
| Model Number | Token2 T2F2-mini |
| Button | Capacitive sensor-type integrated touch-button (on the top of the key) |
| Functions | FIDO U2F + FIDO2.1PRE+ HOTP (HID Emulation) |
| Firmware | FIDO 2.1PRE FT |
| Maximum FIDO2.1 Resident keys | 128 |
| Embedded security algorithm | ECDSA , SHA256, AES, HMAC, ECDH |
| Interface type | USB-A + USB Type-C (with optional adapter) |
| Lifetime | At least 10 years |
| Programming cycles | 100,000 times |
| Communication protocol | CTAP2, HID |
| Management Tools | FIDO2.1 Manager or the fido2-manage command-line tool. Note: This key is not compatible with mobile companion apps. |
| Working voltage | 5.0V DC |
| Input Currency | 35mA |
| Power | 0.18W |
| Working temperature | -10℃ - 50℃ |
| Storage temperature | -20℃ - 70℃ |
Integration guides
Using Your T2F2 Security Key with Google
Passwordless authentication in Azure AD with Token2 FIDO2 keys
FIDO U2F security key for Stripe
Using FIDO2 USB keys under Linux
Operating Systems and Browsers Support
For detailed information on how FIDO2 authentication is supported across different operating systems and browsers, including specific considerations and limitations, please visit our comprehensive guide
Blog
21-12-2025
Android, NFC, and the Missing Piece of WebAuthn
 For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
09-12-2025
Framework ExpansionCard Enclosure for Token2 Keys
 Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.